Newsletter

October 2018

September 2018

August 2018

July 2018

June 2018

May 2018

April 2018

March 2018

February 2018

January 2018
Helpful Tools
Explore practical tools designed to give you clearer visibility, stronger security, and smarter decision making. These resources help simplify complex IT challenges, surface risks early, and turn data into actionable insights you can use with confidence.

BetterTracker
Track your IT spending, identify cost optimization opportunities, and understand where technology budgets are allocated across your organization with real-time analytics and automated reporting.

DMARC Tester
Test your email authentication settings, identify vulnerabilities in your domain configuration, and prevent email spoofing attacks that damage your reputation and compromise security.
Get Phishing Scanner
Helpful Videos
How to Spot Phishing Scams and Avoid Dangerous Links
Understanding Ransomware: How It Works and How to Prevent It
Password Best Practices: Building Strong, Secure Passwords
Get Phishing Scanner
Cybersecurity Awareness


eBooks

10 Disaster Planning Essentials for A Small Business Network
This report reveals how you can protect your business from common data loss disasters.

6 Immediate Security Protections Every Business Should Have
Find out how you can avoid falling victim to hackers and cyberattacks.
AI Resources
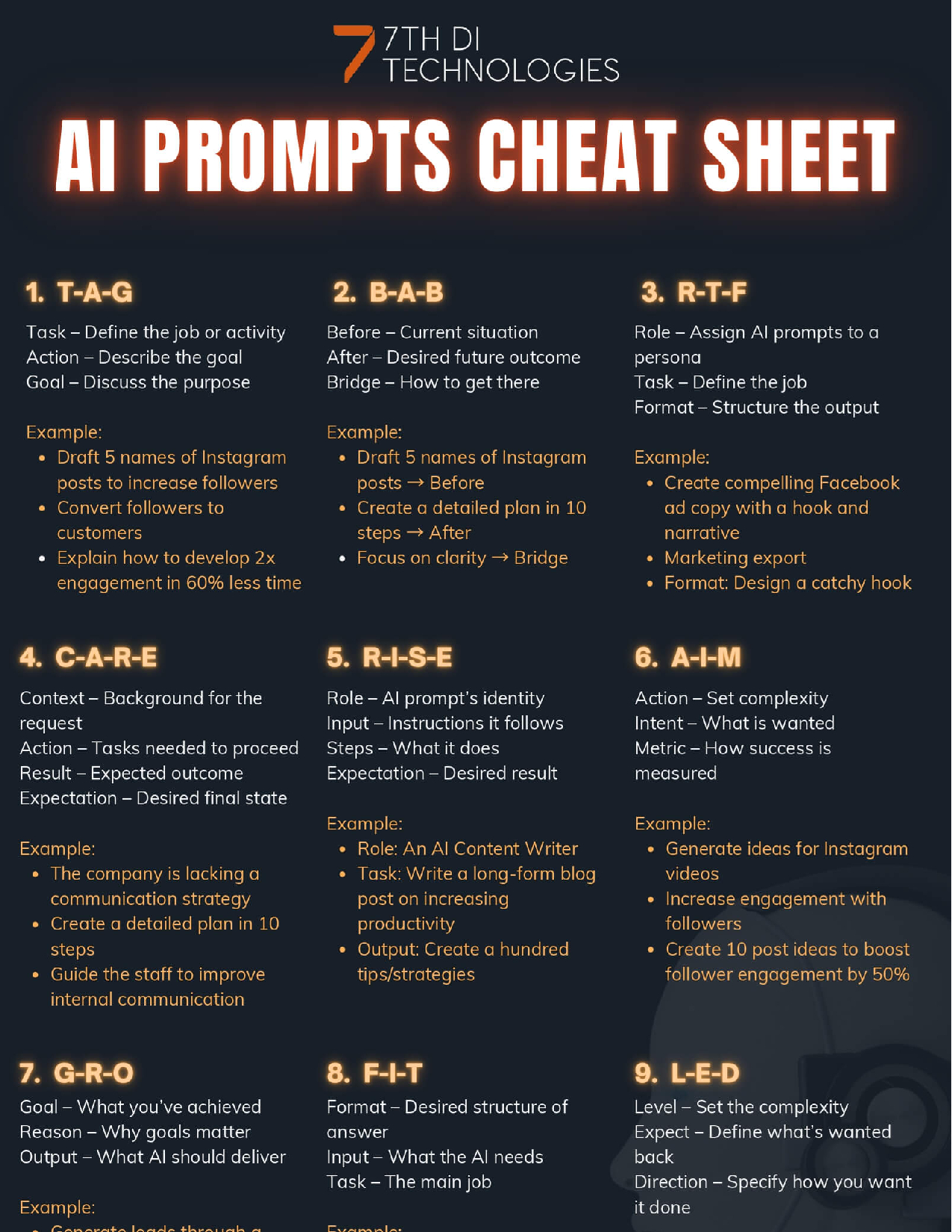


Our Podcast
Mission Over Money
Tools
Wireshark
A network protocol analyzer that captures and inspects data traveling through a network in real-time, helping identify vulnerabilities and troubleshoot network issues.
Metasploit
An open-source penetration testing framework that allows security professionals to test system defenses, find weaknesses, and improve security by simulating attacks.
Nmap (Network Mapper)
A network scanning tool used for discovering devices on a network, scanning for open ports, and identifying vulnerabilities, often used in network audits and security assessments.
Kali Linux
A Debian-based Linux distribution with a suite of pre-installed security tools for penetration testing, forensics, and reverse engineering, commonly used by cybersecurity professionals.
© Copyright 2026 7th Di Technologies. All Rights Reserved. Built with MSP Sites. | Privacy Policy
